In the vast universe of Kubernetes, managing configuration data and sensitive information is paramount for ensuring smooth operations and maintaining security. This is where ConfigMaps and Secrets come into play, serving as essential tools for Kubernetes administrators and developers. Let's delve into what ConfigMaps and Secrets are, their significance, and how to effectively utilize them in your Kubernetes deployments.
Understanding ConfigMaps and Secrets
ConfigMaps: ConfigMaps are Kubernetes objects designed to store non-sensitive configuration data in key-value pairs. These configurations can include environment variables, command-line arguments, configuration files, or any other settings required by your applications running within the cluster. ConfigMaps provide a convenient way to decouple configuration from containerized applications, making it easier to manage and update settings without modifying the application itself.
Secrets: Secrets, as the name implies, are used to store sensitive information such as passwords, API keys, TLS certificates, and other confidential data. Unlike ConfigMaps, Secrets are stored in an encrypted format to ensure security and prevent unauthorized access. Kubernetes handles the encryption and decryption of Secrets, allowing you to securely manage sensitive information within your cluster.
Example: Spaceship Control in Kubernetes
Imagine you're commanding a futuristic spaceship represented by your Kubernetes cluster. Each component of your spaceship, represented by containers, requires specific configuration data to operate efficiently. Here's how ConfigMaps and Secrets come into play:
ConfigMaps act as a repository for general configuration settings. For instance, you might have a ConfigMap storing engine throttle settings, navigation coordinates, and communication protocols.
Secrets, on the other hand, safeguard critical information like launch codes, access credentials to restricted areas, and encryption keys. These Secrets are encrypted and only accessible to authorized entities within the cluster.
Task 1 :
Create a ConfigMap for your Deployment
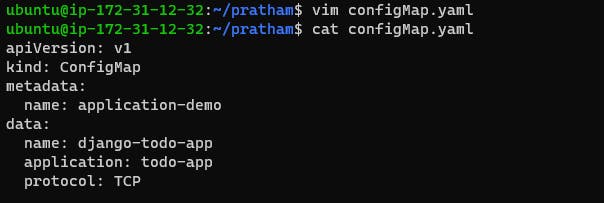
In this example, the apiVersion specifies the version of the Kubernetes API that is being used, and the kind specifies that this is a ConfigMap resource. The metadata section includes information about the ConfigMap, such as its name. The data section is where the key-value pairs are defined.
You can create the ConfigMap by running the following command:
kubectl apply -f configmap.yaml
Update Deployment: Modify your deployment YAML file to include the ConfigMap data as environment variables .
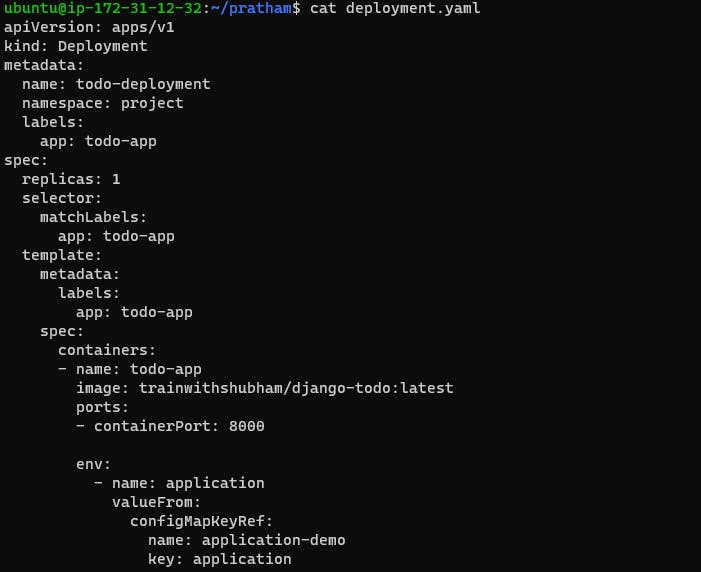
Apply Changes: Execute kubectl apply -f deployment.yml -n <namespace-name> to apply the updated deployment configuration.
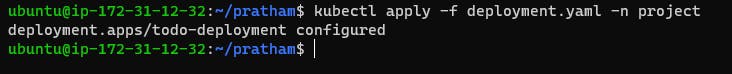
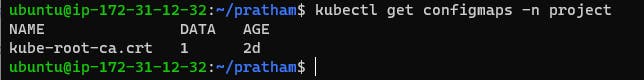
Verification: Confirm the creation of the ConfigMap by checking the status of ConfigMaps in your namespace (kubectl get configmaps -n <namespace-name>).
Task 2 :
Create a Secret for your Deployment
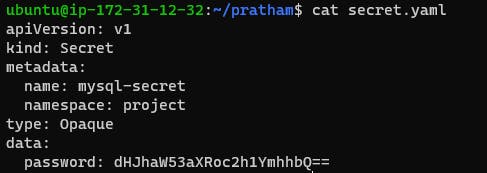
In this example, the apiVersion specifies the version of the Kubernetes API that is being used, and the kind specifies that this is a Secret resource. The metadata section includes information about the Secret, such as its name. The type specifies the type of the Secret, which is Opaque in this case. The data section is where the key-value pairs are defined, with each value being base64 encoded.
You can create the Secret by running the following command:
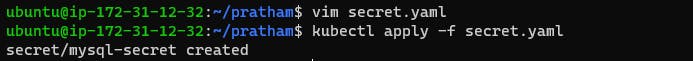
Update Deployment: Update your deployment YAML file to reference the Secret for accessing sensitive information securely.
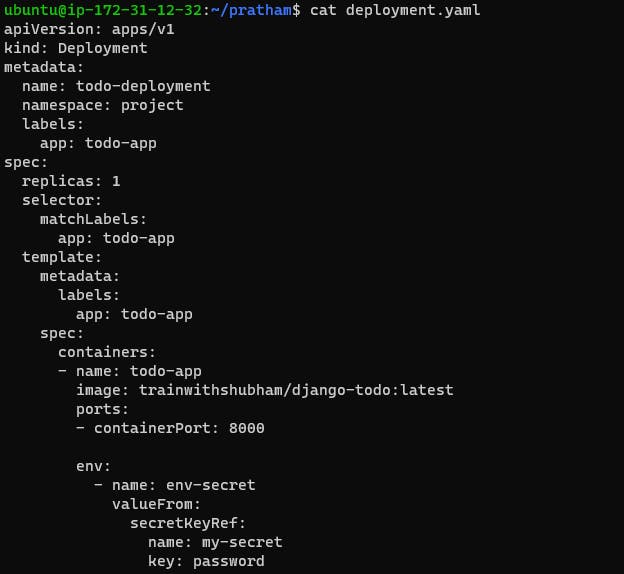
Apply Changes: Apply the updated deployment configuration using kubectl apply -f deployment.yml -n <namespace-name>.
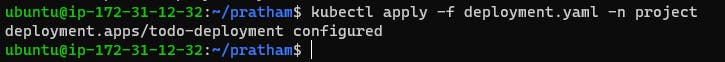
Verification: Check the status of Secrets in your namespace to verify that the Secret has been successfully created (kubectl get secrets -n <namespace-name>).
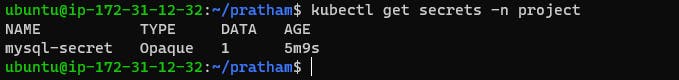
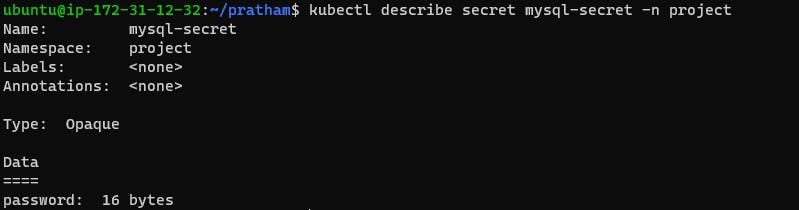
You can also use the following command to view the details of a specific Secret:
kubectl describe secret <secret-name> -n <namespace-name>
By completing these tasks, you're effectively harnessing the power of ConfigMaps and Secrets to streamline configuration management and enhance security within your Kubernetes environment.
I'm confident that this article will prove to be valuable, helping you discover new insights and learn something enriching .
thank you : )